WANNACRY
May 12, 2017
1BTC:$1676.993800
- Artist
- Samantha Asri
- Fact Date
- May 12, 2017
- Fact #
- 094
- Printing Specifications
- Paper / Stock
- Xper paper
- Print Finishes
- Clear UV
- Page Size
- 70cm x 35cm
In 2017, ransomware went viral with the spread of WannaCry, software that locked up business computers and demanded payment in BTC. North Korean hackers were found to be responsible and not for the last time. It was a motif that was to dominate global cyber attacks for years to come.
In the late 2010s, a new type of cyber attack began to cripple global organisations: ransomware. Rather than stealing company data, hackers would simply encrypt it and then levy a hefty fee, paid in bitcoin, for the victim to have it decrypted. This was digital piracy on an industrial scale. One of the most sophisticated implementations surfaced in 2017 in the form of WannaCry.
WannaCry’s deadliness stemmed from a composite design that merged a ransomware payload with a potent worm-like propagation engine that could spread autonomously and indiscriminately across the globe. The malware was programmed to seek out and encrypt file types that included documents, photos, databases, and archives.
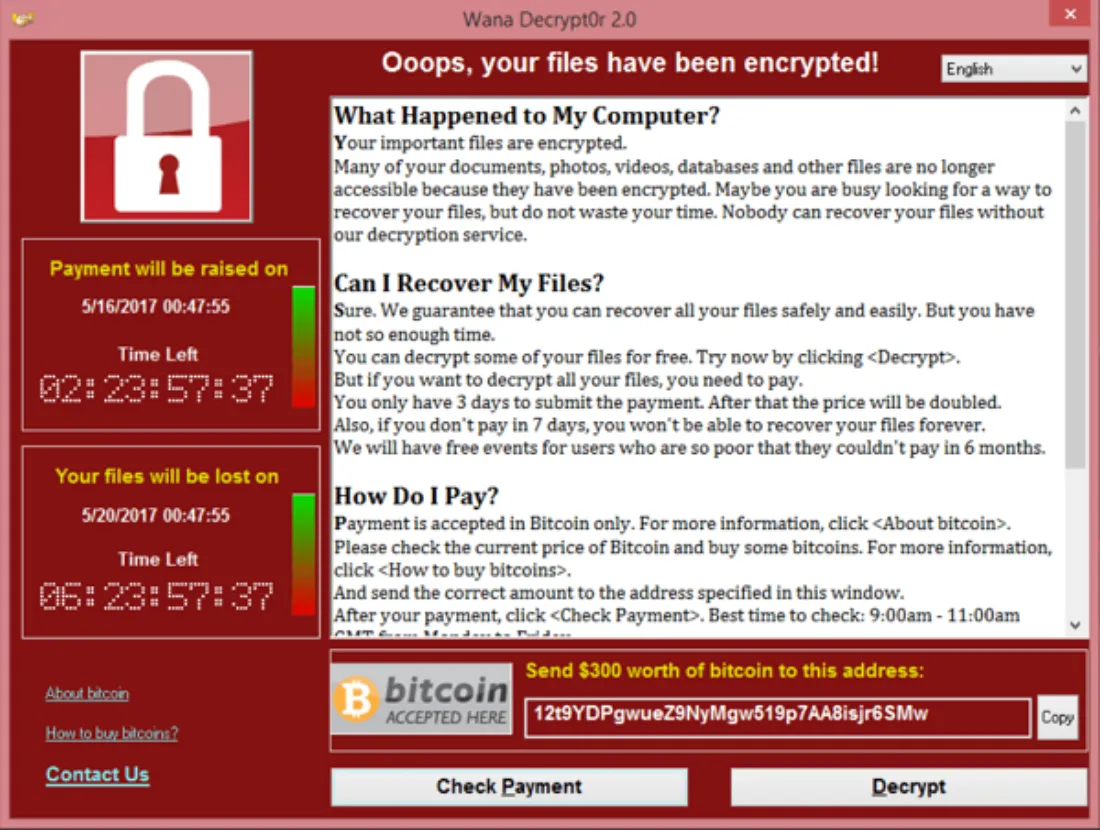
Upon successful encryption, WannaCry demanded an initial ransom of $300 in BTC, which would double to $600 if not paid within three days. After seven days, the malware threatened to delete the files permanently. To prove that decryption was possible, the interface offered to decrypt a small sample of the victim's files for free. This was elaborate trolling, combining emotional blackmail with good old-fashioned extortion.
By exploiting a Microsoft vulnerability, the worm carrying the WannaCry payload was able to propagate with ruthless efficiency. Soon, businesses and users the world over were being forced to buy their first bitcoin if they wanted their files back. This was not the awareness campaign the Bitcoin community would have wanted but there was no denying its virality.
The Contagion Spreads
On May 12, 2017, WannaCry unleashed havoc on global networks, starting in Asia before spreading across Europe. High-profile casualties included Spanish telecommunications giant Telefónica and the UK's National Health Service. By late morning, images of hijacked departure boards at German railway operator Deutsche Bahn, displaying the WannaCry ransom note, provided a visible manifestation of just how far – and fast – the attack had spread.
While the contagion was halted later that day when a security researcher discovered the WannaCry kill switch, the fallout from the incident rumbled on for months. And it didn’t take long before the finger of blame was being pointed at a rising North Korean hacker collective known as Lazarus Group.
Their most audacious attack to date might have been a relative failure, but they were quick learners. The group rapidly pivoted away from noisy, indiscriminate ransomware to focus on state-sponsored cryptocurrency theft. Likeliest culprit Lazarus Group went on to steal billions of dollars in digital assets with their attacks growing in scale and sophistication. Cryptocurrency was no longer the payment mechanism: it was the target.
While WannaCry was devastating in terms of spread, as a piece of ransomware it flopped. Despite infecting hundreds of thousands of computers and inflicting as much as $4B in economic damage, the attackers collected a pittance – while very few victims actually got their files back due to WannaCry’s flawed payment mapping.
The malware’s three hardcoded Bitcoin wallets received only 327 payments worth around $130,000 (51.62 BTC). Still, as a viral stunt that forever connected the idea of ransomware and cryptocurrency, it was wildly effective. WannaCry was the proof of concept that spawned a slew of imitators. Bitcoin was born in code, but this was a software innovation it could have done without.
- Artist
- BTC On this day
- May 12, 2017
- Market Cap
- $27,379,103,877
- Block Number
- 466,103
- Hash Rate
- undefined TH/s
- Price Change (1M)
37%
- Price Change (3M)
66%
- Price Change (1Y)
268%
